Which Blockchain?
The Bitcoin White Paper was published by Satoshi Nakamoto in 2008; the first Bitcoin block got mined in 2009. Since the Bitcoin protocol is open source, anyone could take the protocol, fork it (modify the code), and start their own version of P2P money.
This open-source quality of the Bitcoin blockchain contributed to the fact that, over the years, the Bitcoin protocol has been modified hundreds of times to create alternative versions of Bitcoin that are either faster or more anonymous, like “Zcash” and “Litecoin”. At some point, it became clear that the underlying blockchain protocol provides an operating system that allows a group of people who do not know or trust each other to organize themselves around specific objectives, not only money without banks.
Many projects, therefore, tried to use blockchain technology for other types of P2P value transfers, like decentralized file storage without Amazon Web Services, as in the case of the “Sia Network“, or social networks without Facebook, Twitter, and the like, as in the case of “Steemit”. The idea emerged to move away from single-purpose blockchains that only have one smart contract, and instead create a protocol where you can build any type of P2P transaction on the same blockchain. Some of the most interesting early projects were “Colored Coins” and “Mastercoin”. Their idea was to use Bitcoin as a transaction token for any kind of economic transaction or legal contract. Vitalik Buterin, who was involved in those projects for some time, realized that these adaptations of the Bitcoin blockchain were possible but not efficient and flexible enough. Subsequently, he introduced the idea of decoupling the smart contract functionalities from the blockchain functionalities and started the Ethereum project.
The Ethereum Network hereby provides a more flexible development environment than the Bitcoin blockchain, and derived special-purpose blockchains. It is a P2P network that can process any type of smart contract, which can be easily created with a few lines of code, and without the necessity of creating your own special-purpose blockchain infrastructure. Unlike Bitcoin, which is designed for a single function (P2P remittances) with a single smart contract, the Ethereum blockchain is designed as a decentralized computer network on which any kind of smart contract can be programmed, enabling any kind of direct exchange of value.
As opposed to Bitcoin and other single-purpose blockchains, Ethereum decoupled this smart contract layer, which now runs on top of the underlying Ethereum blockchain, making it easy to create smart contracts with just a few lines of code. The emergence of Ethereum inspired many newer blockchain projects to develop similar smart contract networks. Examples of such projects include: “Cardano”, “Neo”, “EOS”, “Hyperledger Fabric”, and many more. There are many factors that will be relevant for the assessment of their feasibility – technical, economic, and legal factors. It is still unclear which alternative solutions to Ethereum will become popular, if there will be a “winner takes all” scenario, or whether we will have multiple standards to work on.
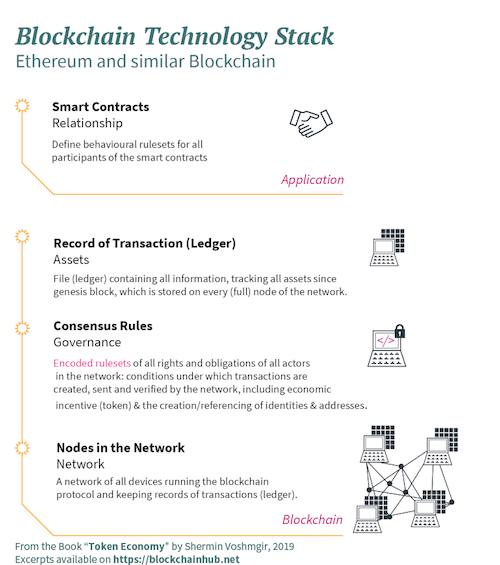
For now, Ethereum seems to have the biggest traction, and the first-mover advantage with many developers, but this can change quickly. Furthermore, alternative distributed ledger technologies have emerged with completely different types of consensus mechanisms, like directed acyclic graphs (DAGs), for example, that do not require the creation of a chain of blocks anymore, and instead use alternative cryptoeconomic mechanisms to reach consensus. Projects like “IOTA”, “Byteball”, or “Nano”, for example. On the other hand, private institutions like banks, insurance companies, and many supply chain-heavy industries realized that the concept of collective data storage and management by a distributed ledger could be very useful as an industry collaboration tool. As opposed to public and permissionless blockchains, however, the industry started to design permissioned blockchains, where all validators are members of a consortium, or at least separate legal entities of the same organization.
However, the term “blockchain” in the context of permissioned and private ledgers is highly controversial and disputed. Critics question whether a permissioned ledger, where you have trust by authority, should be considered a blockchain at all. Proponents of permissioned or private blockchains argue that the term “blockchain” may be applied to any data structure that batches data into hashed blocks of transaction. While public ledgers create trust by math, with a consensus mechanism that incentivizes individual behaviour to achieve a collective goal, permissioned ledgers are centrally managed and do not use “trust by math.” They use “trust by default of a legal contract,” or “trust by reputation.” However, the least common denominator, whether public or private, is the principle of distributed data storage and data verification. This is why the term “distributed ledger technology” (DLT) emerged as a more general term to describe technologies that have derived from the Bitcoin blockchain. They might be permissioned, or as in the case of IOTA, for example, not use a blockchain at all.
Alternative Consensus Mechanisms to PoW
Bitcoin’s “Proof-of-Work” is groundbreaking, as it resolved the “Byzantine Generals Problem”, but it comes at a cost. While it guarantees security in an untrusted network, it is slow, energy-intense, and favours those who have more economic resources to spend. This is why many researchers and developers started to explore alternative consensus mechanisms, building on this groundbreaking concept of “Proof-of-Work,” while trying to tackle some of Bitcoin’s major challenges.
The research questions that need to be resolved are:
- How do we reach consensus on one version of history that the majority accepts as true? What is the economic incentive to collaborate? What are the payoff mechanisms (economic incentives) to make sure everyone keeps the system intact?
- How can one align scarce natural resources (like electricity and CPU) with network resources to prevent malicious actors from spamming the system with bad behaviour?
- Where does security come from?
- What are security risks and attack vectors?
Even though many different consensus algorithms are being experimented with, “Proof-of-Work” and “Proof-of-Stake” are currently the most widely spread consensus mechanisms. However, it is important to note that different blockchains using the same general consensus mechanism might have different specification.
Proof-of-Stake
Proof-of-Stake is a consensus mechanism where only network actors who have a financial stake in the network could add the blocks in the blockchain. Instead of sacrificing energy to validate a block, users must prove they own a certain amount of the network tokens to generate a block. Holding tokens in a wallet represents one’s stake. There are many variations of “Proof-of-Stake” implementations.
Early PoS proposals assumed that those who have more stake in the system have a natural incentive to act in a truthful manner when validating transactions and writing blocks. Token holders should have an interest in the success of that network; otherwise, their stake in the system would devalue if they contributed untruthfully. It was assumed that the more of the token one owned, the more one had at stake if the network was attacked. Voting rights were therefore proportional to the amount of stake held in the network. However, there is a problem in the original “Proof-of-Stake” mechanism: as opposed to PoW, where mining is costly, and it is therefore not smart to waste your energy on a fork that won’t earn you any money, PoS doesn’t have such a provision.
While in PoW it is computationally expensive for a validator to build on every possible fork, the opposite is true in Proof-of-Stake. One does not need computationally intensive work to create a block. It is assumed that the validator has nothing to lose but a lot to win. “Peercoin” was the first project to introduce “Proof-of-Stake.” Other implementations that followed are found in Tendermint (“Cosmos”), Ouroboros (“Cardano”), “Tezos”, “Dfinity”, “Nxt”, “BlackCoin”, “NuShares/NuBits”, “Qora”, each of which have different properties. Some like “Decred” combine elements of both “Proof-of-Work” and “Proof-of-Stake.”
The Ethereum project is planning to transition from “Proof-of-Work” to “Proof-of-Stake” with a hard fork, referred to as Casper, and have developed different proposals of how this should be done:
- Casper FFG (Friendly Finality Gadget), a hybrid version of PoS and PoW, where validators create checkpoints after every 50 blocks, which creates a new genesis block;
- Casper TFG (The Friendly Ghost), which requires validators to put a certain amount of ETH as a deposit to be able to create blocks. Any malicious attempt by the validator may invoke a smart contract to destroy the deposited amount. This proposal is based on the assumption that fear of penalty will keep the validators in check to stay honest, thereby resolving the nothing-at-stake problem.
Delegated Proof of Stake (DPoS) & Other Variants of PoS
Delegated Proof of Stake (DPoS) as implemented by “BitShares” for the first time, is a more radical variation of PoS. Validators don’t compete with each other to create a block of transactions. It is a kind of representative democracy where token holders (stakeholders) can vote for the validator. Token holders do not vote on the validity of single blocks, they vote to elect delegates to do the validation on their behalf. There are generally between 21–101 elected delegates that might be shuffled periodically or given an order to deliver their blocks in. This means that a panel of trusted parties is established, where all members can create blocks and prevent non-trusted parties from creating blocks. Instead of competing on validating blocks, there are designated time slots for each delegate to publish their block.
Token holders can withdraw their vote for a delegate, if delegates continually miss their blocks or publish invalid transactions. By partially centralizing the creation of blocks, DPoS is able to run orders of magnitude faster than most other consensus algorithms. Delegates cannot change transactions, but they can veto specific transactions from being included in the next network block. Different networks use 73 their own variation of DPoS, examples of which are “Steemit”, “EOS”, and “Lisk”.
There are even more variations of “Proof-of-Stake,” most of which are only conceptual or have been implemented by one network only: “Leased Proof-of-Stake,” “Transactions as Proof-of-Stake,” “Proof-of-Importance,” “Proof-of-Capacity,” “Proof-of-Weight,” “Proof-of-Authority,” “Proof-of-Elapsed-Time.”

Byzantine Fault Tolerance et al.
Another group of consensus mechanisms are variations of Byzantine Fault Tolerance, like Federated Byzantine Agreements (“Stellar”, “Ripple”), Practical Byzantine Fault Tolerance (“Hyperledger Fabric”), and dBFT (Delegated Byzantine Fault Tolerance) as used in, “NEO”. Some more alternative protocols use a combination of mechanisms, such as Hashgraph (asynchronous Byzantine Fault Tolerance, Gossip Protocol, Virtual Voting).
DAGs
Furthermore, there is a whole series of protocols that use Directed Acyclic Graphs (DAGs), like “IoT Chain”, “Byteball”, “Block Lattice” (Nano), and “IOTA” (Tangle). The consensus mechanism of DAGs is fundamentally different from blockchains. Instead of bundling data together into blocks that are then confirmed one after another, Directed Acyclic Graphs require newly added data to reference and validate past data. Usually, each new transaction would have to reference and validate two transactions that came before. In doing so, the network comes to form a graph of converging and confirmed transactions. If one were to incorrectly validate a past transaction, one‘s own transaction would fail to be confirmed by other participants. Explaining each of the consensus mechanisms listed above in detail is beyond the scope of this book and would require a dedicated book on comparing different consensus mechanisms. Academic literature on these protocols is still scarce, and many of these protocols are experimental. Some don’t have proper documentation and are being used by one project only, sometimes without being properly researched, or without having undergone the academic peer-review process.
With or without a Token?
With the advent of derived technologies using modified governance rules to the original Bitcoin protocol, it seems necessary to classify different distributed ledger solutions. The main distinction is designed around the question of who is allowed to
- validate transactions
- write transactions to the ledger, and
- read transactions.
Depending on the type of ledger, the answer will vary. To keep things simple, we can say that in public networks anyone can validate, write, and read transactions. Whereas in private networks, only invited members can validate, write, and read transactions. Hybrid variations are also possible. An example would be that validation and writing to the blockchain is invite-only, but reading at least selected transactions is public.
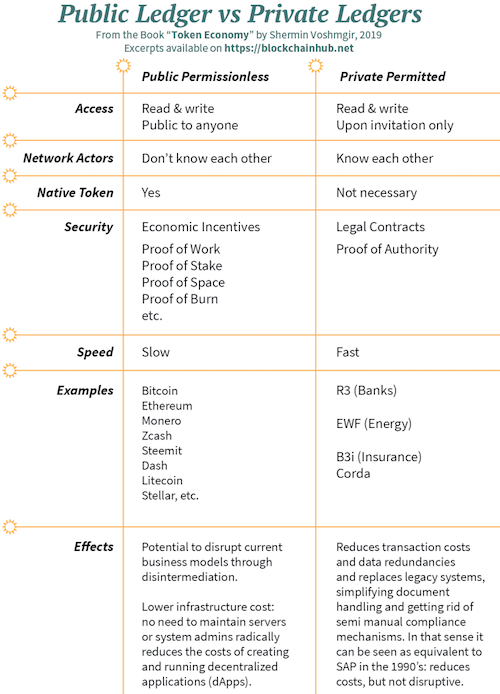
Public and permissionless blockchain protocols are designed on the assumption that everybody is potentially corrupt, and that the least common denominator is money. The cryptoeconomic mechanisms allow for the creation of a new type of global governance tool, steered by economic incentives tied to the creation of the native token. The role of the native token is to encourage a disparate group of people who do not know or trust each other to organize themselves around the purpose of a specific blockchain or similar public ledger, without the need of centralized institutions. The token is, therefore, an integral part of the incentive scheme. In a public blockchain, anyone without the permission of a centralized entity can:
- Run a full node on their local device, validating transactions in the network, by simply downloading the code from the Internet.
- Mine a block of transactions, writing data to the blockchain, thus participating in the consensus process (“Proof-of-Work”), and earning network tokens in the process, by simply installing an application on their device.
- Download a wallet and send transactions through the network and expect to see them included in the blockchain if they are valid.
- Use public block explorer software to see all transactions that happened on the blockchain, or conduct chain analysis (big data) on all blockchain-related data stored on a full node.
While tokenized incentives make the untrusted networks safe, they also make them very slow. Public and permissionless networks can only handle a few transactions per second, which makes them unfeasible for large-scale applications with high transaction volumes. At the time of writing this book, Bitcoin and Ethereum can only handle less than a dozen transactions per second, yet Visa and similar settlement solutions would require hundreds of thousands of transactions at peak time. However, various technological solutions are currently being proposed to resolve these scalability issues.
Another question revolves around how trust in this network is generated:
- Algorithmic trust, or
- Trust by default of a legal contract.
Public networks, for the lack of existing legal relationships, require algorithmic trust guaranteed by consensus mechanisms like “Proof-of-Work.” All nodes participating in the consensus protocol are untrusted, as they are not known beforehand. The consensus mechanism for such a setup has to account for maliciousness.
The token is an essential mechanism component to make this network of untrusted actors attack-resistant. Private and permissioned ledgers, on the other hand, have a federated setup with bilateral contractual agreements. It’s an invite-only members club. The network is not accessible to arbitrary participants. Members trust each other because they have bilateral contractual agreements with each other, and if anything goes wrong, they know who to sue. Permissioned ledgers, therefore, do not need a token to incentivize coordinated action, whereas it is integral to permissionless networks. The fact that the identities of all participating nodes are known beforehand provides a natural protection against “Sybil attacks.” Private and permissioned ledgers can, therefore, settle much more transactions per second, as they don’t have to deal with an unknown amount of anonymous nodes. They also provide more privacy than current state of the art public blockchains.

Permissioned ledgers are mostly used by industry consortia. Transaction verification is conducted by a pre-selected set of participants, for example, sixty financial institutions, each of which operates a node, and where forty must sign every block in order for the block to be valid. Depending on the industry and use case, the right to read data of the ledger may be public, partially public, or restricted to the participants. While most blockchain literature makes a binary distinction between permissioned and permissionless, I would like to argue that there is no such thing as 100 percent permissionless.
Every consensus mechanism requires a minimum threshold of investment that one needs to make in order to be able to validate transactions or write to the ledger. Most of the world population does not have the economic means to purchase specialized hardware powerful enough to mine Bitcoin. Even for a full node that only validates transactions in a public blockchain, and does not require the same level of hardware investment as a mining node, one would need to invest into a regular PC. At the time of writing this book, buying a PC means that one would have to spend at least a few hundred EUR13 to validate transactions. While 500 EUR is not much money for an average European household, it surpasses the monthly income of a considerable part of the world‘s population. Not to mention the costs needed for a mining computer.
“Proof-of-Stake”-based consensus is public, but not entirely permissionless. The consensus mechanism requires you to own a minimum amount of network tokens to be eligible to validate transactions. “Permissionless” is, therefore, a relative term that we cannot use in a binary way, but rather as a gradient, ranging from less permissioned to fully permissioned. In such an early stage of blockchain technology, permissioned solutions can be useful in highly regulated industries that want to build on a distributed ledger, but are subject to government regulation. Industry advocates claim that federated solutions can provide higher levels of efficiency, security, and fraud problems of traditional financial institutions.
It‘s not very likely that private blockchains will revolutionize the financial system, but it will probably replace legacy systems, making the industry more efficient. It might also be a stepstone into a wider adoption of public and permissionless blockchain infrastructure, once the underlying technology becomes more scalable and mature, better understood by regulators, and people develop more know-how and trust. It is unclear how the technology will pan out in the medium-to-long run. Some predict that permissioned ledgers might suffer the fate of Intranets in the early 1990s when private companies built their own private networks because they were afraid to connect with the public Internet. Over time, this fear disappeared. Today, Intranets are used in very limited cases where high levels of security are required.
Trending Technologies 2020
Why SAFEBOXTM Document Sharing is Ideal for Your Professional Needs
As a notary public, you are tasked with handling numerous legal procedures, each involved with different types of documents. Without a legitimate document sharing platform, your job can become tiring due to a lack of an efficient file sharing technique. Furthermore,...
Easy Document Sharing for Notary Publics with SAFEBOXTM
SAFEBOXTM gives you a platform to handle all your document sharing responsibilities hassle-free. It's easy, fast, secure, and reliable. As a notary public, you get to deal with sensitive information daily. SAFEBOXTM ensures that all your data is secure from...
Trends in Document Sharing Technology
The world is undergoing a fast-paced change in technology, which is revolutionizing how things around us work. In particular, the 21st century has seen a proliferation in smart devices, with new inventions coming up every day. One factor that has been subject to...
Security Issues with Document Sharing Technologies
Today, the corporate world is undergoing a swift change in operations, a feat that has been greatly influenced by technological advances. Employees are using different techniques to transfer important documents to clients and fellow workers. This has revolutionized...
How Can Blockchain Technology Improve Data Storage?
Decentralized Cloud Storage Cloud storage systems maintain data on remote servers that are accessible from the internet. However, unlike conventional cloud servers, decentralized cloud storage does not keep user data on a single centralized server. A decentralized...
Our Latest Updates

Why SAFEBOXTM Document Sharing is Ideal for Your Professional Needs
As a notary public, you are tasked with handling numerous legal procedures, each involved with different types of documents. Without a legitimate document sharing platform, your job can become tiring due to a lack of an efficient file sharing technique. Furthermore,...
Easy Document Sharing for Notary Publics with SAFEBOXTM
SAFEBOXTM gives you a platform to handle all your document sharing responsibilities hassle-free. It's easy, fast, secure, and reliable. As a notary public, you get to deal with sensitive information daily. SAFEBOXTM ensures that all your data is secure from...
Trends in Document Sharing Technology
The world is undergoing a fast-paced change in technology, which is revolutionizing how things around us work. In particular, the 21st century has seen a proliferation in smart devices, with new inventions coming up every day. One factor that has been subject to...





